By: Robert Bisewski
robert.bisewski@thinklogicly.com

October is for pumpkin spice lattes and spooky decorations and it’s also Cybersecurity Awareness month!
It’s a collaborative effort led by the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA) to raise awareness about digital security and protecting individuals and firms from cybercrime.
Internet access and data management is vital to every company, yet both can potentially expose vulnerabilities. This can lead to serious virtual attacks that put the company at the mercy of hackers if anything ever goes wrong. The most common threats include:
- Malware
- Data breach
- Denial of service
- Cyber fraud
- Phishing
These threats can occur when cybercriminals are successful in finding errors, loopholes and vulnerabilities that they can exploit to steal user data and identities.
Cybersecurity Treats to Avoid Cybercriminal Tricks
Cyber attacks are increasingly common for banks, government agencies, and FinTech companies. Another type of victim emerged: the critical infrastructure of a water processing facility in the UK. A ransomware gang infiltrated the company’s IT security systems and stole 5TB of data.
According to an E&Y survey of over 5,000 consumers on the topic of financial institutions winning the battle on trust:
- 37% of respondents now say a FinTech firm is their most-trusted financial services brand
- 51% of Gen Z and 49% of Millennials named a FinTech as their most-trusted financial brand
With the convenience of contactless payments, mobile banking, micro-investing, online lending, and other features, comes an increased risk of cyber theft of valuable personal and financial data of consumers and firms alike.
The threat landscape has changed. This imposes a number of challenges for FinTech, in particular key areas like:
- Properly managing the security of employee access and internal system access
- Protecting customers during login and while they use a company’s product
- Mitigating ongoing and possible threats with rigorous company-wide processes
- Ensuring continuity in the event of a breach and potential data loss
All are vital to a safe and maintainable internal IT system. Preparing in advance for possible threats is critical for the survival of any publicly-facing infrastructure.
The Nightmare Before VPN
Access is an essential aspect in IT services. Restricting what or who can and cannot obtain access to certain files, servers, and internal components is a hallmark of solid architecture.
Modern Cloud paradigms have simplified this security-by-design philosophy, though at times these are still somewhat suboptimal. A common solution to restrict connections is to use a Virtual Private Network or “VPN”. The two most popular VPN software programs in the industry are OpenVPN and Wireguard.
Placing all important infrastructure behind such a network and requiring staff to be connected to a VPN for system-level access makes it difficult for non-employees to gain access.
In addition, restricting employee access using LDAP (Lightweight Directory Access Protocol), the process of securely managing users and their access rights to IT resources, and Cloud User Profiles can reduce the risk of an employee’s computer being compromised, since they themselves do not have full access.
Less Spooked, More Protection
Ultimately, companies offering these security products to end-users is critical. Consumers need to be convinced that firms take all possible steps to ensure the safety of data and accounts. Simple, confidence-building strategies:
- the implementation of a two-factor authentication (2FA) system
- encrypting the data at-rest on the backend database instances
- restricting which servers have access to which databases via firewall rules or Cloud security groups
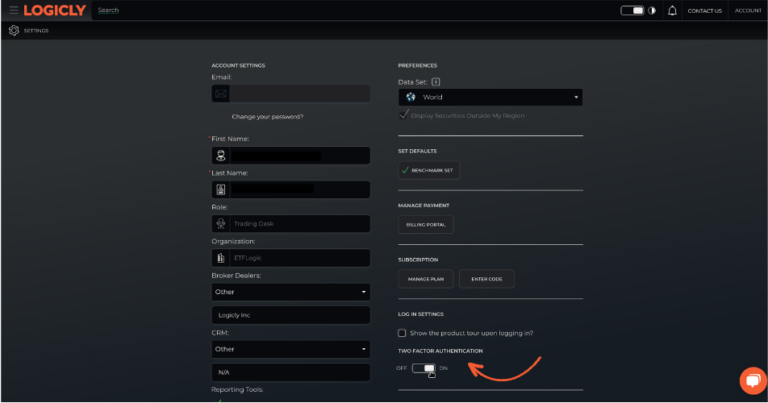
At LOGICLY, we make it as easy for our clients to protect themselves while using our portfolio management technology through two-factor authentication. In “Account Settings”, clients can enable 2FA, which sends an email with an authentication code each time the client logs in.
Data loss, while awful to contemplate, is a tragic statistic in the internet-connected world. Worse still, a data breach by hackers can be devastating, especially if there are no backups and might be affected by ransomware.
A starting point is backing up critical data to a location far removed from the rest of the infrastructure. This reduces risk and may allow firms to restore its system to working order if a breach occurs.
Network segmentation and restricting connections between servers (either via a physical router or Cloud security groups) can also help. If one server is compromised or hacked, then the rest of the infrastructure remains safe.
With these basic concepts in place, companies may begin their journey sooner rather than later toward a safer and more dependable system, which will help save them in the long-run. The financial costs of cyber crime pale in comparison to the reputational risk and costs associated with an exodus of clients.
Enjoy reading this article? Other content you may find interesting:
- Getting paid…in Bitcoin?
- The Future is Here: How Thematics is Disrupting Investing
- Beach Bum or Desk Jockey
- Harley Davidson, Sustainability, and ESG
- Women, Millennials, and Financial Planning
- How to Use One of Wall Street’s Best-Kept Secrets
To connect about media inquiries or to discuss the article, please email Robert at: robert.bisewski@thinklogicly.com